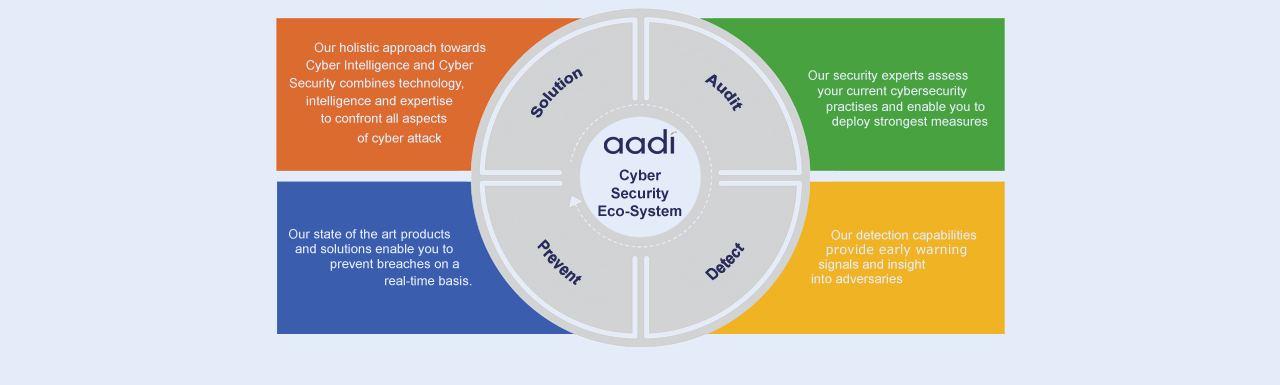
Cyber Security Solutions
Services
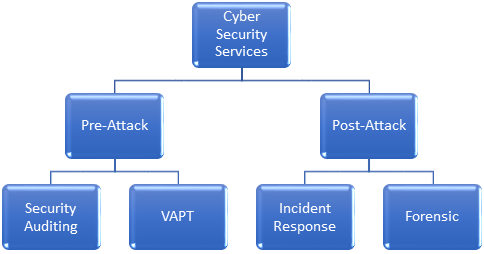
SECURITY AUDITING
AADI Security Audit services offer clients a thorough, cost-effective means of evaluating their overall information security posture in order to identify vulnerabilities and make informed remediation decisions, guided by AADI experience and expertise–and in doing so ensure that their networks, systems, data and customers are protected from the rising tide of cybercrime.
AADI security auditors work with the adequate knowledge of the audited organization, in order to understand the resources to be audited. We provide IS audit service complying with IS audit standards, guidelines, and best practices to assist your organization in ensuring that your information technology and business systems are protected and controlled.
Some of the services AADI offers are
|
|
VULNERABILITY ASSESSMENT AND PENETRATION TESTING (VAPT)
AADI offers internal and external penetration tests as separate services. These tests mimic the action of an actual attacker exploiting weaknesses in network security without the usual dangers. The internal penetration test examines internal IT systems for any weakness that could be used to disrupt the confidentiality, availability, or integrity of the network. The external penetration test examines external IT systems in the same manner.
|
|
INCIDENT RESPONSE
AADI comprehensive threat detection and cyber incident response services help to maintain business continuity. By detecting advanced persistent threats (APTs) and providing swift, clear and confidential remediation advice, our solutions help to minimize cyber security risk.
AADI's Incident Response (IR) and forensics services provide industry-leading outsourcing of cyber security incident handling to trained professionals in order to minimize the impact of incidents to business continuity.
AADI Incidence Response services are targeted for customers with assets considered a target for potential attackers — those businesses and entities with a clear threat landscape.
The AADI Incident Response Team is an international team of senior and principal IT security consultants with years of experience. Incident response and forensics cases are knowledge-intensive and rely heavily on having experienced, trained professionals at hand. All investigation activities are planned, performed, and properly documented to support business recovery actions taken by the customer after the investigation is over.
FORENSIC
AADI’s digital forensics group can help your organization obtain, preserve, and examine digital evidence. Our forensics analysts piece together specific events to provide a greater understanding of when an event occurred, who was involved, and what data was affected.
We also help clients involved in litigation by supporting digital evidence and data collection and acquisition across IT systems, mobile devices, and social networks, as well as providing investigative analysis, expert testimony, and litigation consulting.
Our services include
|
|
Response
CERT- AADI — AADI’s official computer emergency response team monitor online activity 24/7 in order to identify and respond to any incidents or security breaches
Investigation
An experienced investigation team capable of identifying suspects, collecting and analyzing evidence