1. 360-view - view provides real-time visibility and comprehensive controls on all your Windows assets across multi-cloud environments. This is a Comprehensive Cyber Security Solution that Enables Total Control of your assets. This ultimate solution to simulate any type of Breach Attack Simulation (BAS) on all end points to find resilience factor for APT attacks. Our ultra-light sensor brings greater visibility and efficiency to your organization with insight & manageability as security begins and ends at endpoint.
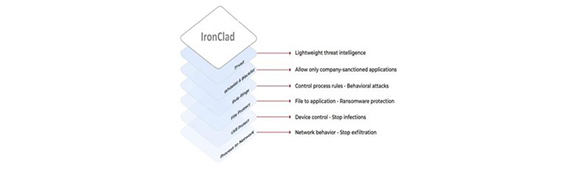
2. IronClad - product helps to reduce time and effort spent investigating false positives Leverage whitelisting, blacklisting, and configurable security rules to achieve proactive security Centrally deploy and manage agents across thousands of endpoints in minutes and with minimal configuration efforts Adopt different levels of security based on the type and purpose of endpoints Protect ATM kiosks, point of sale systems, medical devices, and general-purpose systems Securely lock down legacy desktops and servers that run unpatched software.
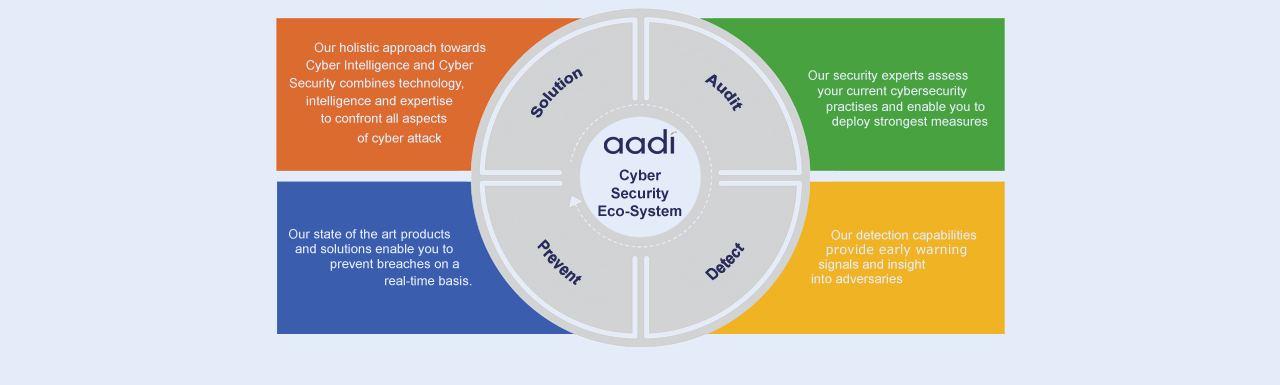
We Offer:
- 24/7 monitoring of events and alerting of security incidents
- Log management and Threat detection
- Incident Response
- SIEM platform configuration including fine-tuning of rules, creation of custom use-cases and dashboards
- Reports
- Log parsers
- Threat Intelligence Service
Aadi Defence has all the Cybersecurity solution(s) that are 100% compliant and will help a city achieve baseline security measures required by the Standard Operating Procedure (SOP) for Cyber security of Smart City Infrastructure at all 4 levels.
Aadi Defence has all the Cybersecurity solution(s) that are 100% compliant to the above directives and will help central/ state govt/ UTs to achieve baseline security measures required to enhance cybersecurity preparedness for Ministries, Departments and other associated Government Organizations and help them to make strong, safe, secure and resilient cybersecurity system for Government.
- A unified real time platform to integrate various application on unified platform.
- Reports are easy to store, user friendly access and present with a click of mouse.
- All the historical reports are available with defined user's policy
- Predict events of mass agitations.
- Build a 360 degree profile from leaked databases and social media.
- Identify fake propaganda and BOTs
- Identify illegal trade of drugs and weapons on Dark Web.
- Perform Link Analysis between multiple suspects and radical outfits.
- Monitor public opinion & sentiment.
- Monitor channels of mass communication including WhatsApp, Telegram, etc.
- Identify profiles of suspects on social media through Facial Recognition.
- Perform geo-analysis to gather location based intelligence.
Aadi Defence brings a proven Forensics Analytical Toolkit Premium which enables agencies to quickly analyse huge volumes of data, correlate different data sources together and generate immediate alerts for actionable intelligence for:
- Computer Forensics.
- Mobile Forensics.
- Imaging and Analysis
Aadi Defence simulates Cyber Lab with Red and Blue Skill Training, Scenarios, Ethical Hacking, Network Security, Cyber Forensics. The range enables security professionals to learn best Infosec skills and knowledge in a controlled environment:
- Recognize patterns for security threats and compromise.
- Recognize threats faster and practice responding to them properly.
- Simulate critical infrastructure components, including computer servers and clients.
- Simulate and conduct offensive operations against enemy targets.
- Simulate and conduct defensive operations to protect critical infrastructure Components.