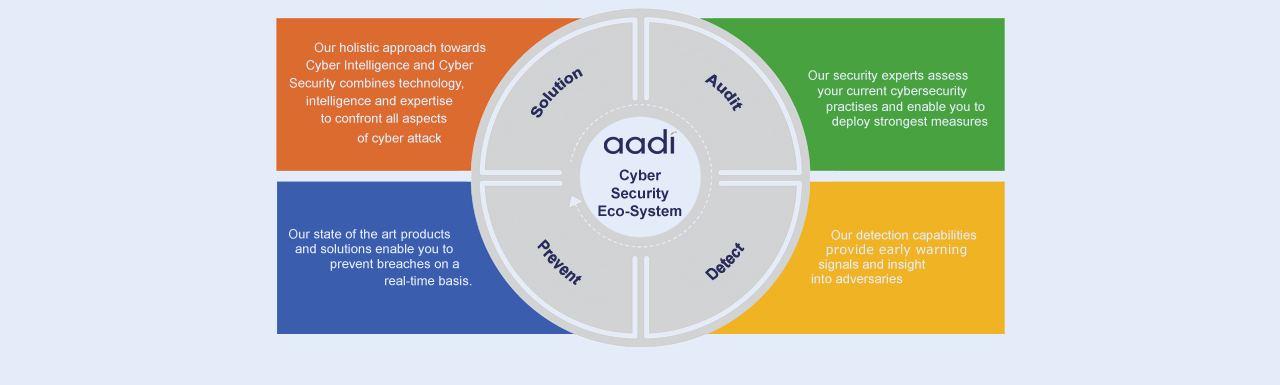
Cyber Security Services
Prevention
Security Assessment
|
|
Solid experience
|
|
- AADI has experience auditing the most established banks and ambitious startups, energy giants and small law firms, which help us, understand weaknesses of any size and sector IT infrastructures.
- Irrespective of your company’s size, we guarantee an individual approach, high quality expertise and absolute confidentiality.
- Our experience in vulnerability analysis has taught us to pay attention to small details that can have a big impact.
- We don’t believe in the “black box” methodology, giving preference to a deep analysis of your systems’ internal logic.
- This methodology enables us to see risks overlooked by our competitors and offer sustainable solutions to minimize the risks.
- We speak the language our client can easily understand: each report contains a short summary developed for the company’s top managers together with a detailed description of vulnerabilities and specific recommendations for your technical specialists.
- We are not a systems integrator, that’s why our recommendations don’t come in the form of expensive hardware changes, but rather changing system settings, or refactoring sections of code.
Our Specialization
|
|
|
Brand Protection
Antipiracy
We protect digital content including movies, music, software, mobile applications and computer games
 |
Know your enemy
|
 |
Act promptly
|
 |
Attack accurately
|
 |
Archieve results
|
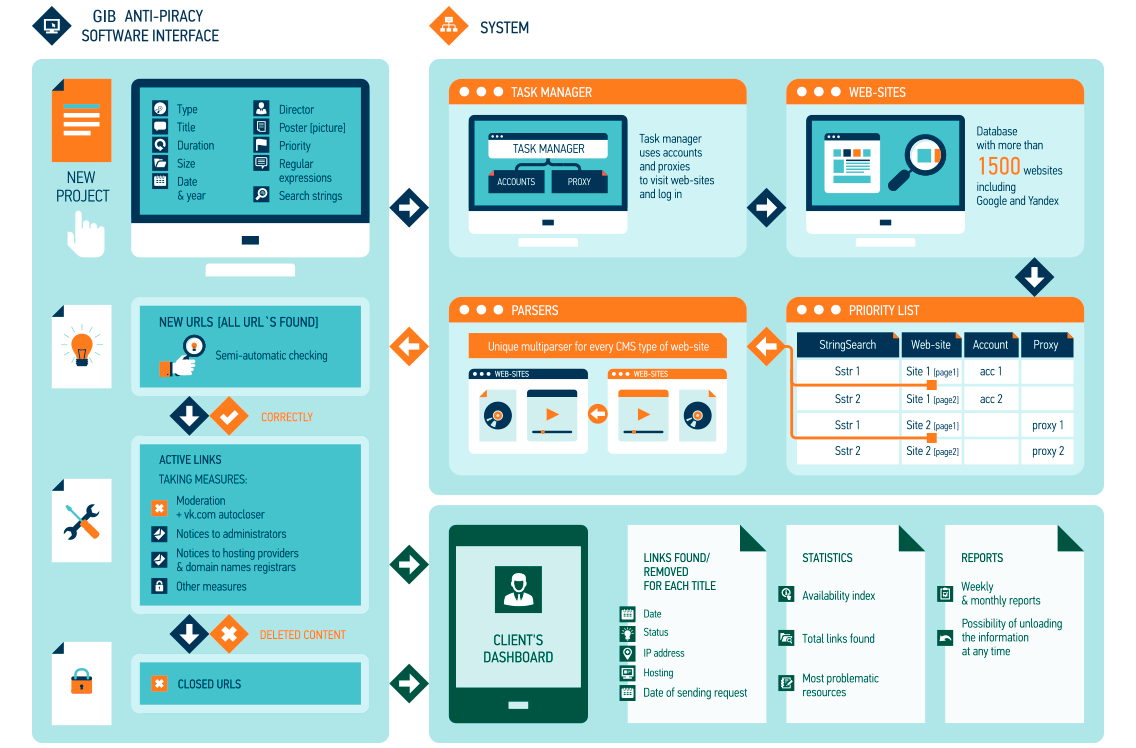
Antifraud & Anticounterfeit
We monitor and rapidly respond to the misuse of your brand and identify and eliminate internet sales channels and sources of counterfeit goods
Monitoring and prevention of online brand abuse
AADI Brand Protection offers a range of online brand protection services based on AADI’s unique threat intelligence data and extensive experience in IT incident investigation and response.
ADVANCED MONITORING TECHNOLOGY
AADI’s automated system designed to monitor Cyber-crime infrastructure and hacker interrelations enables us to be the first to learn about new websites, mobile apps, and announcements abusing your brand. We also monitor tools used for their distribution – email spamming, contextual advertising, SEO manipulations, and bot activity used to rank malicious or brand infringing resources higher in search engines.
REPUTATIONAL RISK MANAGEMENT WITHIN 48 HOURS
Fraudulent websites and mobile applications that steal credentials and money from clients or distribute malware leveraging customer’s trust in your brand are blocked on a priority basis upon AADI request.
SIGNIFICANT REDUCTION IN ONLINE COUNTERFEIT SALES IN ONE MONTH
AADI not only can identify the infringing sites selling your products illegally, but also with our investigative background have the ability to identify the identity of individuals involved.
PREVENTION OF INCIDENT REPETITIONS
Once the criminal is included in the Intelligence database, he will never be able to continue his activity silently. The system will automatically inform us about all his attempts to misuse your brand on other resources at the stage of domain registration and or renting hosts.
AADI`S BRAND AND EXPERIENCE WORK FOR YOU
| HIGHLY EFFICIENT NOTIFICATIONS | EFFECTIVE PRETRIAL MEASURES |
| We file infringement notices to the owners of fraudulent resources using their actual emails instead of sending them to fake addresse often used to register domains and accounts. | When the criminals receive notifications to their personal e-mails, most of them prefer to comply with the demand from a company with a solid reputation in successful Cybercrime investigations. |
| AADI leverages its reputation among hosting providers and domain registrars all over the world and cooperates with Internet management organizations to promptly block dangerous resources in many jurisdictions. |
Full support at every stage of the incident response
ACCURATE BLOCKING REPORTS AND DIGITAL EVIDENCE COLLECTION
We thoroughly collect evidence of copyright and brand infringement and document all communications during pretrial actions to equip you with informative reports and excellent evidence collection to initiate legal actions.
INVESTIGATIONS AND PROFESSIONAL LEGAL SUPPORT IN COURT
The majority of violations are solved out of court. In those cases where it’s impossible, we will be glad to provide you with professional legal support at every stage of the trial.