We are pleased to introduce AADI Defence, a global technology solutions provider, focused on delivering customer value through high-quality and cost-efficient solutions. AADI has been one of the trend setters in global delivery practices with our Customer Centric Model (CCM) for Operations Management and Delivery. Established in 2016, AADI along with its partners has supported global clientele in Fortune 500 and Government Sectors. Our teams provide the entire range of IT and Cyber Security Solutions from strategy consulting to implementation and maintenance, across a range of Sectors.
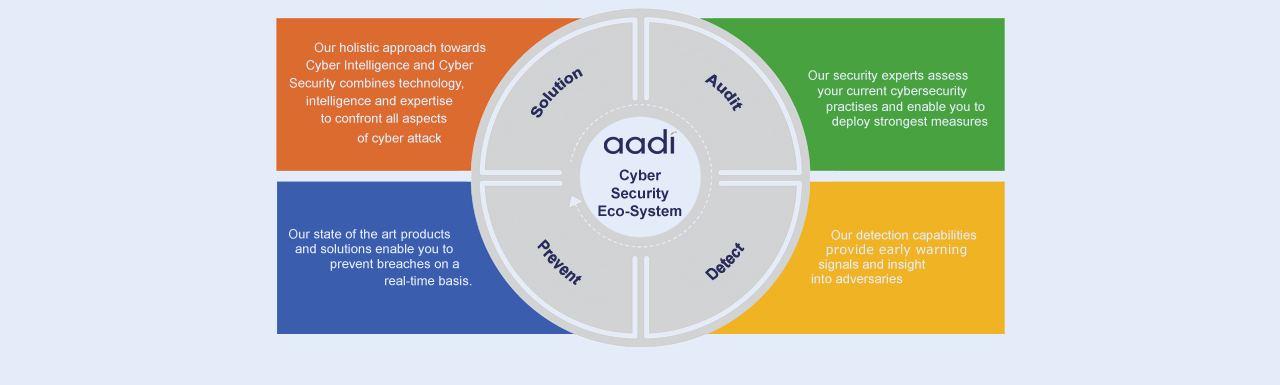
AADI consists of multiple Business Units (BUs), managing different lines of businesses, delivering services in eGovernance, Cybersecurity, Smart Agri - Tech, Clinical Trial Services (i.e. Clinical Data Management (CDM), Statistical Programming (Stats), Medical Writing (MW)), Application Development/Maintenance, Large scale onsite deployment projects (System Integration-SI), Staffing, Staff Augmentation spread across India and USA. Our Off-shore Development Centre is certified with CMMI Level 5, ISO 9001, and State-the-art infrastructure with ISMS 27001 and SOC2 Certified Information Security Management, possessing a robust BCP/ DR site. AADI has various Application Services and its Systems Integrations Division has been delivering IT solutions to various clients like Delhi Police, BRBNMPL, NIC, NICSI, TSTS, NHAI, Gurugram & Imphal Smart Cities etc. Cybersecurity practice is one of our prime areas of focus under Government Sector.
This practice focuses on System Integration (SI) and providing SOC managed services to various Government and Enterprise sectors. This practice is helping various organizations with Managed Security Service Provider (MSSP)/ Security Operations Centre (SOC) services, building innovative security products, leveraging technology advancements to help organizations in building strong SOCs with end-to-end Security Orchestration, Automation and Response (SOAR) capabilities in handling cyberattacks proactively in Government and Enterprise sectors. The System Integration (SI) services collaborates with organizations, cities to conduct regular risk assessments, end to end Cybersecurity implementation, operationalization and maintenance.
- It is designed based on Zero Trust
- It proactively protect endpoints from advanced cyberattacks
- It's a new cloud-delivered approach to zero trust security
- It's robust, signature less and works at the kernel level
- It detects, alerts and prevents unauthorized processes running on EndPoints
- It encrypts endpoints end-to-end providing an additional layer of security by making data communications tamper proof.
- Physical audit of each Endpoint/ System
- Scan for all points as per the PHQ guidelines
- Collate the Data in excel sheet from each Endpoint/ System
- Get the report sign off from each PS/ Sub Division/ Branch
- Prepare the Gap Analysis report and submit
- Based on Gap Analysis report update/ upgrade the OS
- Download EPS software to implement polices/ restriction to maintain the Cyber hygiene
- 24/7 monitoring of events and alerting of security incidents
- Log management and Threat detection
- Incident Response
- SIEM platform configuration including fine-tuning of rules, creation of custom use-cases and dashboards
- Reports
- Log parsers
- Threat Intelligence Service
- A unified real time platform to integrate various application on unified platform
- Nullify the scope of errors and manipulation of data
- Reports are easy to store, user friendly access and present with a click of mouse
- All the historical reports are available with defined user's policy
With the ever-increasing number of forensic images, it has become essential for investigative agencies to have a single repository to analyse terabytes of data coming from disparate sources.
Aadi brings a proven Forensics Analytical Toolkit Premium which enables agencies to quickly analyse huge volumes of data, correlate different data sourcestogether and generate immediate alerts for actionable intelligence for
- Computer Forensics
- Mobile Forensics
- Imaging and Analysis
- Predict events of mass agitations
- Build a 360 degree profile from leaked databases and social media
- Identify fake propaganda and BOTs
- Identify illegal trade of drugs and weapons on Dark Web
- Perform Link Analysis between multiple suspects and radical outfits
- Monitor public opinion & sentiment
- Monitor channels of mass communication including WhatsApp, Telegram, etc.
- Identify profiles of suspects on social media through Facial Recognition
- Perform geo-analysis to gather location based intelligence
- Recognize patterns for security threats and compromise
- Recognize threats faster and practice responding to them properly
- Simulate critical infrastructure components, including computer servers and clients
- Simulate and conduct offensive operations against enemy targets
- Simulate and conduct defensive operations to protect critical infrastructure Components
- Setting up Cyberforensic Labs - All states have opened Cyber Crime Depts and meeting them and also Home Secy is vital
- CCTNS (Crime and Criminal Tracking Network & System) upgrade - All states had invested in this solution so along with software (CAS & CIPA) they purchased servers and desktops/laptops. We can suggest endpoint security here
- SCRB (State Crime Records Bureau) - States maintains the repository and they report into State as well as NCRB (National Crime Records Bureau). The records are critical and protected, security need to be revamped here.
- Traffic Modernisation